
REQUEST A DEMO
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

Threatnote
Centralize and streamline your CTI program with Threatnote — the first platform purpose-built to manage the full lifecycle of threat intelligence. From intelligence requirements to finished reporting, Threatnote helps you structure, track, and operationalize every part of your CTI workflow. Gain actionable insights, measure impact, and close the loop with stakeholders — all within a powerful, centralized system designed for real-world CTI teams.
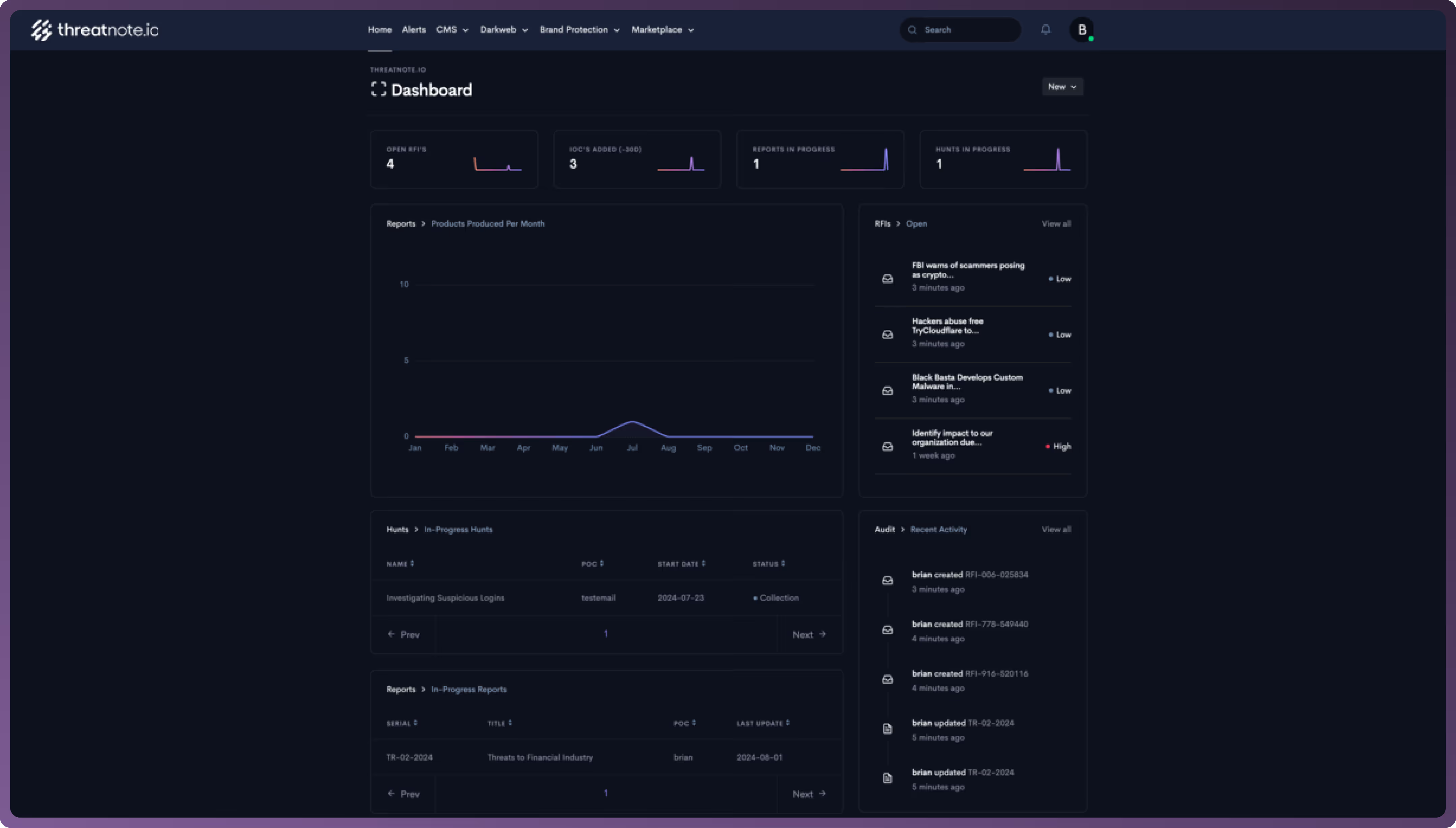














Efficiently handle Requests for Information (RFIs) to ensure quick and accurate responses.

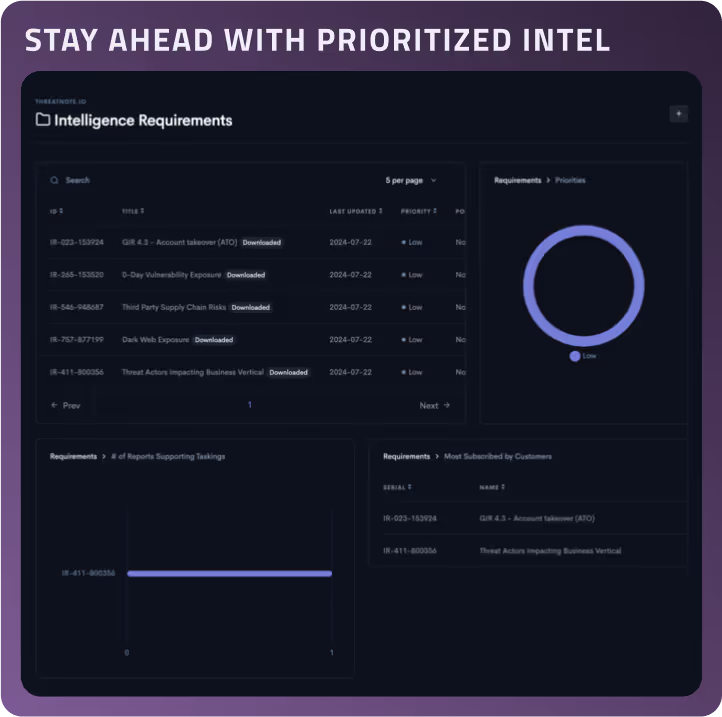
Manage and align Priority Intelligence Requirements with stakeholder needs to focus on what’s most important.

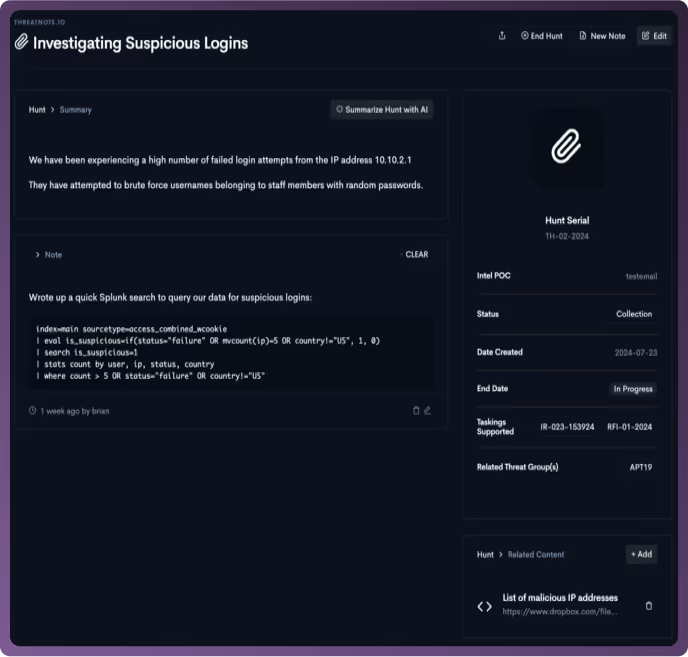
Seamlessly create and execute threat hunts with integrated tools and data.

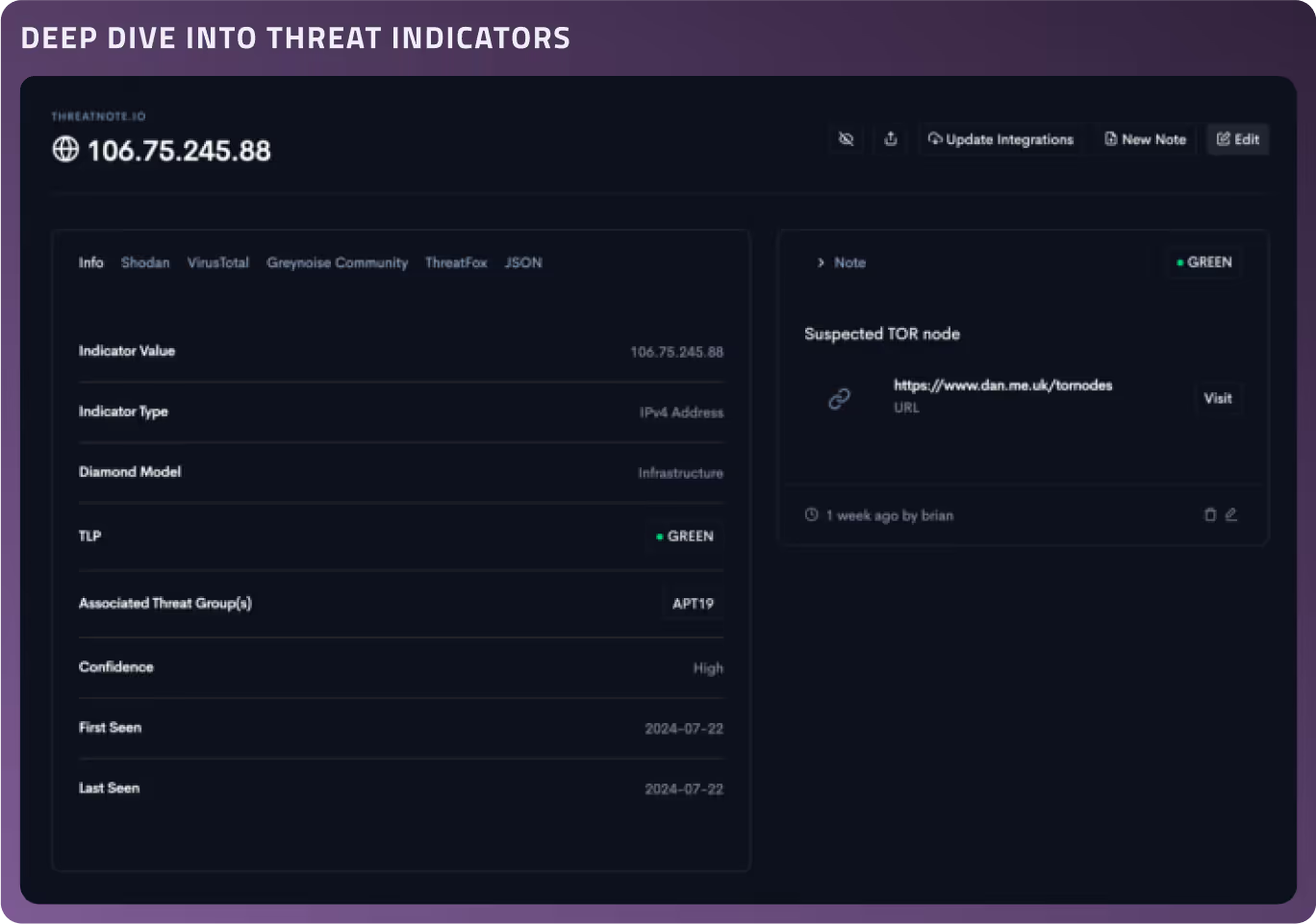
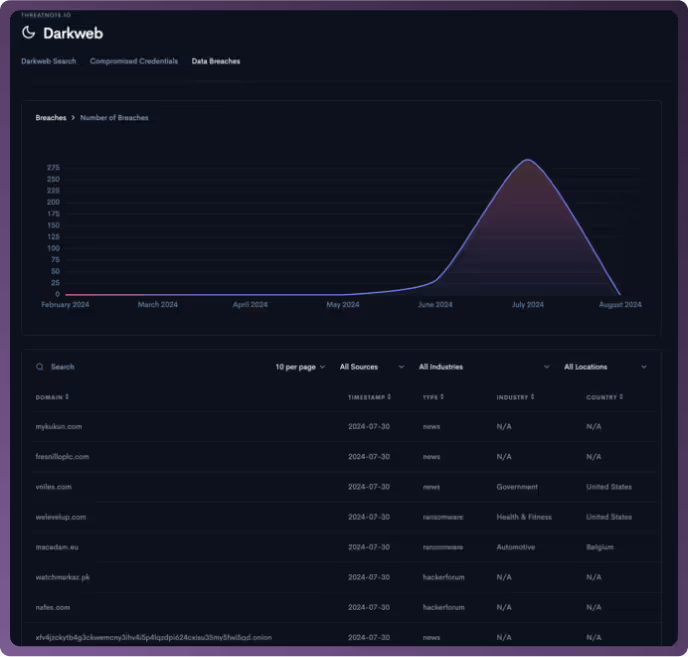
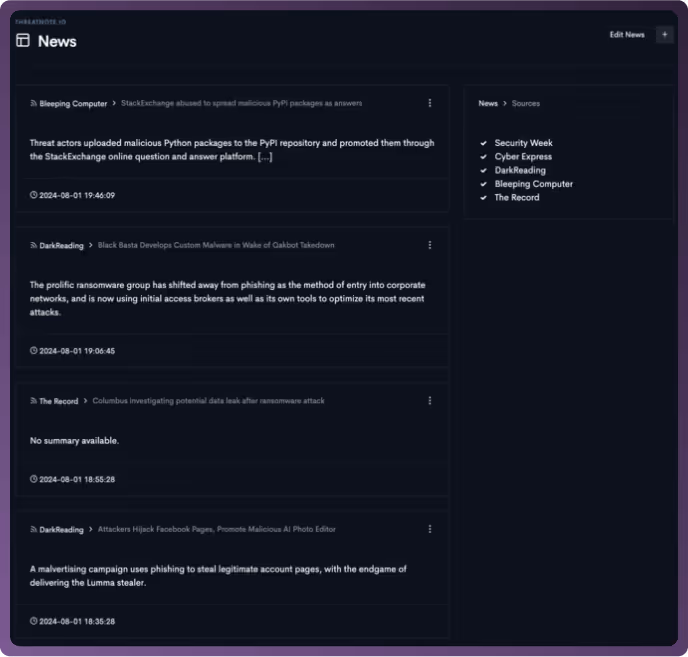
Access a centralized hub for all your dark web data, brand intelligence, and third-party intelligence. Easily track this information and create threat hunts to monitor and address emerging threats.
KEY FEATURES

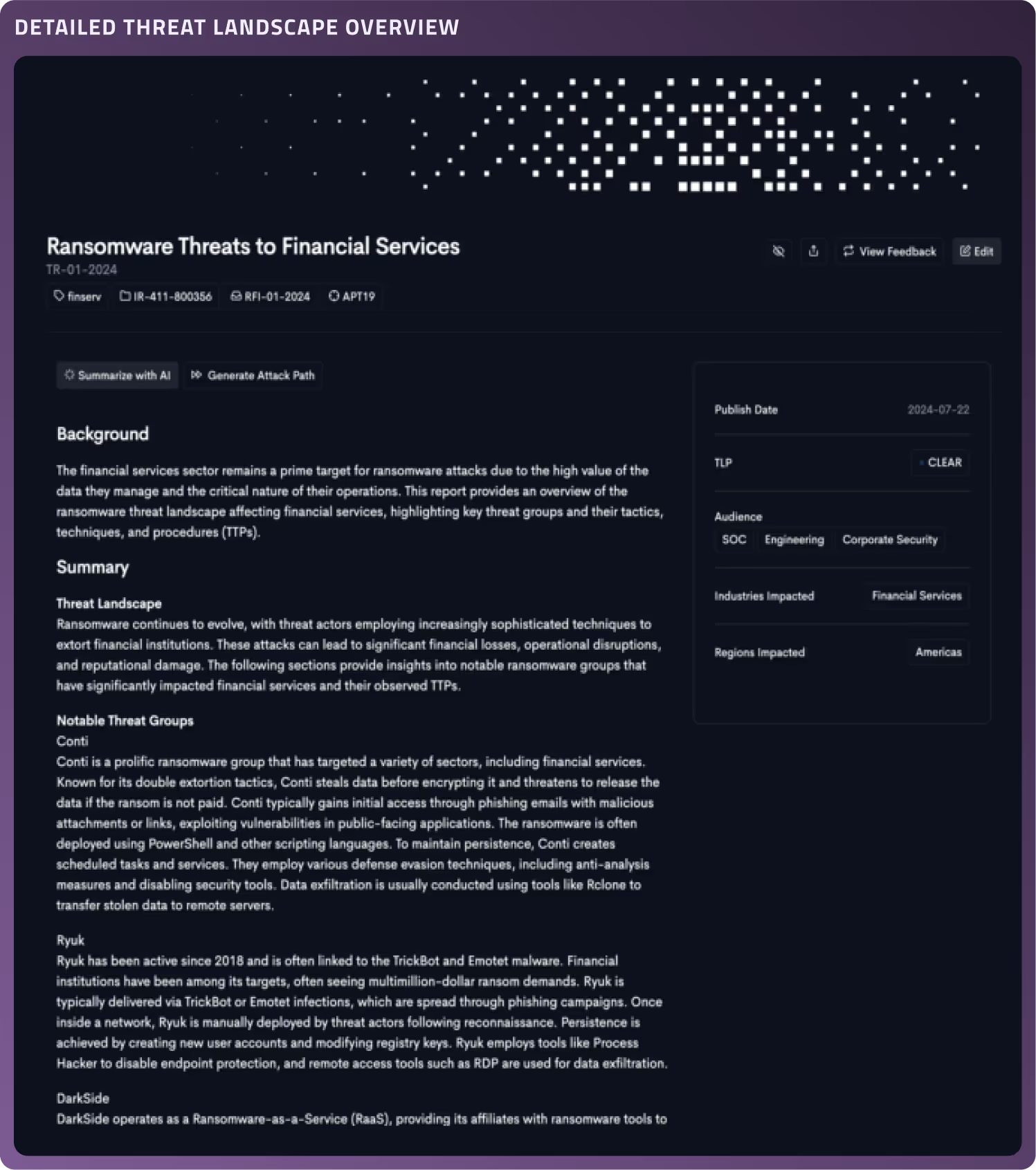
Centralized Threat Reporting
Build and distribute detailed threat reports, all from one place, ensuring clarity and consistency.

Priority Intelligence Dashboard
Monitor and adjust your Priority Intelligence Requirements in real-time to stay aligned with evolving threats.

Marketplace & Peer Collaboration
Enhance your CTI program by accessing marketplace content and connecting with peers to share intelligence and insights.